Emerging Cybersecurity Threats: How Utilities Can Prepare
Emerging Cybersecurity Threats: How Utilities Can Prepare
In today's increasingly interconnected world, the threat landscape for US utilities is evolving at an unprecedented pace. As these vital organizations continue to embrace digital technologies to improve efficiency and customer service, they also find themselves in the crosshairs of malicious actors seeking to exploit vulnerabilities. The realm of cybersecurity is fraught with challenges, and understanding the latest threats is essential for safeguarding critical infrastructure. It is the responsibility of the entire organization to be aware of the most pressing cybersecurity concerns facing utilities, equipping them with the knowledge and strategies necessary to defend against these ever-evolving dangers.
Understanding the Threat Landscape: Targets and Key Actors
In recent years there has been a notable shift in hacker targeting, with a heightened focus on industries such as healthcare, government, and utilities. The indispensable role that US utilities play in providing essential services to Americans makes them enticing targets for a diverse array of threat actors. Any disruption to their operations can have far-reaching and potentially devastating consequences. Cybercriminals often focus on these utilities with the aim of causing service interruptions, financial losses, or even compromising the integrity of the nation's critical infrastructure.
The threat landscape facing utilities includes a spectrum of actors ranging from financially motivated cybercriminals to sophisticated nation-state adversaries. State-sponsored groups from countries like Russia, China, North Korea, and Iran have demonstrated a growing interest in probing the vulnerabilities of American utilities. Their objectives may vary, from intelligence gathering and economic espionage to the potential for future disruption. On the other end of the spectrum, ransomware groups have increasingly turned their attention to utilities, demanding substantial ransoms in exchange for restoring critical services. The rise of these ransomware-as-a-service (RaaS) operations has made it easier for less technically skilled criminals to target utilities, amplifying the threat. Due to the diversity of these actors and their motivations, utilities have had to adapt quickly to adequately prepare and defend against evolving cyber threats.
The Anatomy of a Cybersecurity Attack
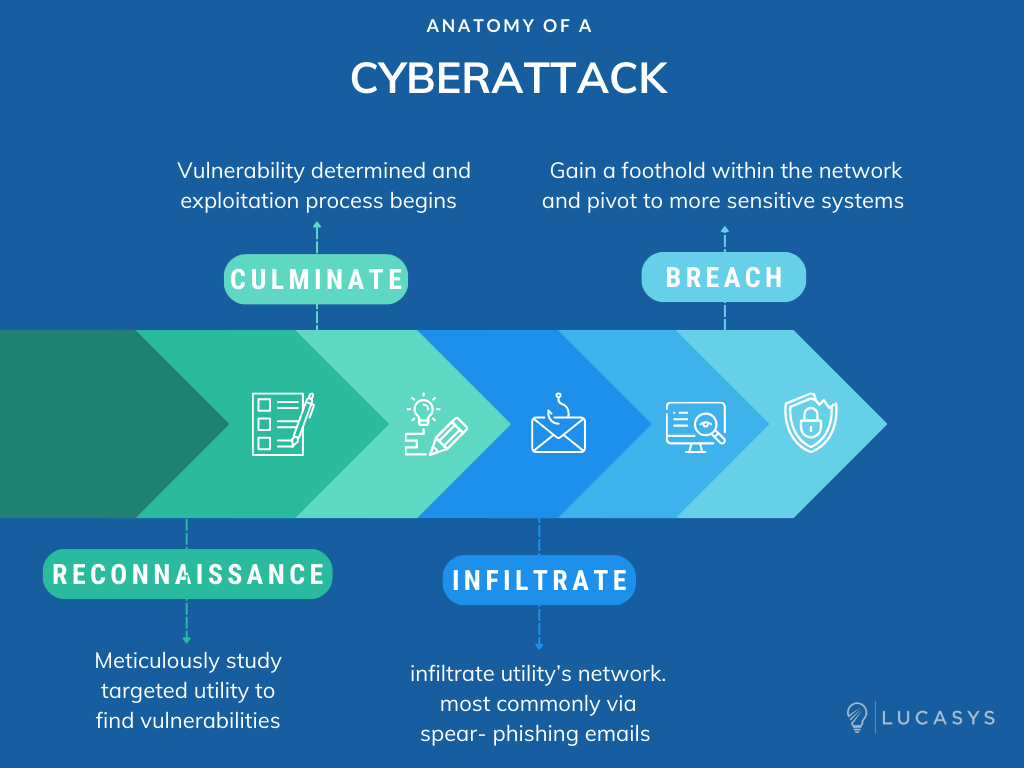
Cyberattacks against utilities often follow a systematic pattern, starting with reconnaissance and culminating in exploitation. Bad actors meticulously study their targets, seeking vulnerabilities that can be exploited to infiltrate the utility's network. One common entry point is through spear-phishing emails that appear legitimate but contain malicious attachments or links. Once an unsuspecting employee clicks on such a link or downloads an infected file, the attackers gain a foothold within the utility's network, from which they can pivot to more sensitive systems. This type of breach is referred to as “social exploitation”.
Some utilities have become familiar with such attacks and have developed robust security measures to prevent such breaches. As a result, hackers are increasingly targeting weaknesses in third-party software used by utilities. Utility providers rely on a multitude of specialized software applications, and when these third-party solutions have unpatched vulnerabilities or weak security configurations, they become prime targets for cybercriminals seeking unauthorized access.
One surprisingly common problem results from the fact that third-party software vendors typically have standards of practice that compel them to publish any security flaws found in their products so that their customers are made aware of any potential risk. Unfortunately, there have been several instances in recent years where security flaws were published by software vendors before the flaw was patched, which is tantamount to advertising security vulnerabilities. Hackers have been quick to take advantage of published security weaknesses, and the customers of the software developers are the ones that become exposed. A prime example of such an attack was the 2023 WordPress attack, during which hackers were able to take advantage of a vulnerability withing 24 hours of the exploit being published by the company.
Fortifying Cybersecurity: Essential Precautions for Utilities
In the face of evolving cybersecurity threats, utilities must prioritize comprehensive security measures to protect their critical infrastructure. This necessitates that they diligently monitor and update all software components within their ecosystem, not just their core systems, and ensure that their third-party providers prioritize robust cybersecurity practices. Failure to do so can leave them vulnerable to exploitation and potentially result in significant service disruptions with far-reaching consequences. Any single software solution that is not being patched regularly constitutes a potential threat to the organization’s entire network, so utilities must choose third-party software with strong security practices and who addresses issues immediately.
Another key strategy is to implement robust network segmentation, isolating critical systems from less sensitive ones to contain potential breaches. This practice limits the lateral movement of attackers, making it more difficult for them to access key infrastructure components. In addition, conducting regular security assessments and penetration testing can help identify vulnerabilities and weaknesses within the network, allowing utilities to proactively address them before malicious actors exploit them. By combining these precautions with a proactive cybersecurity stance, utilities can better defend against the latest threats and safeguard the essential services they provide to the nation.
How Lucasys Can Help
As utilities evaluate their cybersecurity needs, they know they can rely on Lucasys for cutting-edge software solutions built with today’s security challenges in mind. Whether looking for new software or trying to get the most value out of existing solutions, Lucasys can provide insights into the latest accounting and tax issues facing the utility industry. To learn more about how Lucasys can help visit https://www.lucasys.com/solutions.